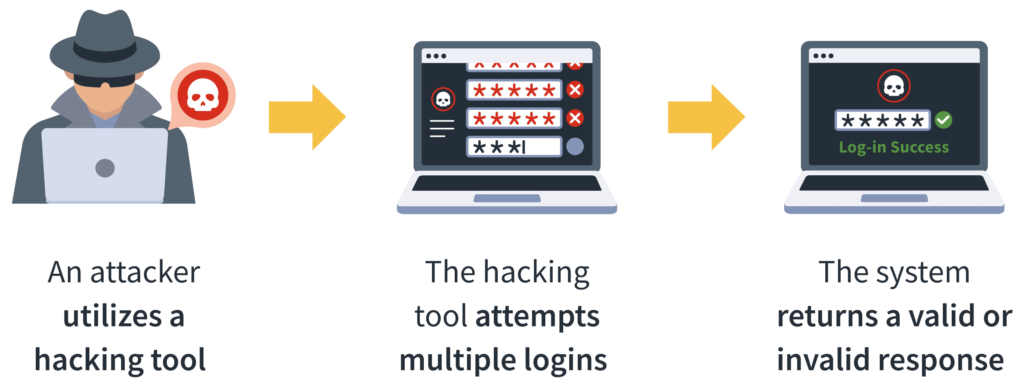
In today’s digital landscape, computer networks and systems are vulnerable to cyberattacks. One of the most common methods used by attackers is a brute force attack, which involves trying to guess a password by systematically trying every possible combination of characters until the right one is found. This method is time-consuming but effective, and it can be used to gain unauthorized access to everything from personal devices to company networks.
To understand how a brute force attack works, it’s essential to know how passwords are stored in computer systems. Passwords are usually encrypted, which means they are translated into a non-readable format, and then stored in a database or file. When someone logs in with their password, the system compares the entered password with the stored encrypted password and, if they match, grants access to the user.
A brute force attacker would try to crack this password by systematically guessing all possible combinations of characters until the right one is found. The attacker could either try all possible character combinations of a given length (i.e., all possible five-letter passwords), or, more commonly, use a list of commonly used passwords, a dictionary, or a list of passwords obtained from previous data breaches.
Brute force attacks are used to access everything from personal devices to enterprise networks. Attackers can gain access to a system by guessing passwords on user accounts or administrator accounts. Once the attacker has access, they can steal sensitive data, install malware, or use the network to launch further attacks.
In recent years, brute force attacks have become more sophisticated with the use of powerful computers and algorithms that can guess passwords more efficiently. Attackers have also started using social engineering tactics to trick victims into giving up their passwords willingly or downloading malware that could steal passwords.
To protect against brute force attacks, individuals and organizations should use strong passwords and two-factor authentication. Strong passwords should be long, unpredictable, and include numbers, letters, and special characters. Two-factor authentication adds an additional layer of security by requiring a second piece of information, such as a code sent to a mobile device, to log in.
TL;DR
Brute force attacks are a common way for attackers to gain unauthorized access to computer networks and systems. They work by systematically guessing passwords until the right one is found. To protect against these attacks, use strong passwords and two-factor authentication. By doing so, you can reduce your risk of falling victim to a cyberattack.